Introduction:
Internet of Things (IoT) is a concept which enables communication between internetworking devices and applications, whereby physical objects or ‘things’ communicate through the Internet. The concept of IoT began. with things classified as identity communication devices. Radio Frequency Identification Device (RFID) is an example of an identity communication device. Things are tagged to these devices for their identification in future and can be tracked, controlled and monitored using remote computers connected through the Internet. The concept of IoT enables, for example, GPS-based tracking, controlling and monitoring of devices; machine-to-machine (M2M) communication; connected cars; communication between wearable and personal devices and Industry 4.0. The IoT concept has made smart cities a reality and is also make self-driving cars.
IOT Definition:
The Internet is a vast global network of connected servers, computers, tablets and mobiles that is governed by standard protocols for connected systems. It enables sending, receiving, or communication of information, connectivity with remote servers, cloud and analytics platforms .
We assume that the Internet is well known and bears no further definition. The question is what do we really mean by “Things ”? Well, things are actually “anything” and “everything” from appliances to buildings to cars to people to animals to trees to plants to industry etc.
A more complete definition, we believe, should also include “Standards” and “Processes” allowing “Things” to be connected over the “Internet” to exchange “Data” using industry “Standards” that guarantee interoperability and enabling useful and mostly automated “Processes
Advantage of IOT:
- Improved Efficiency and Automation
- Data-Driven Decision Making
- Real-time Monitoring and Data Collection
- Predictive Maintenance
- Improved Operational Efficiency
- Enhanced Productivity
- Enhanced Safety
- Remote Monitoring and Control
- Scalability and Flexibility
- Cost Savings
Major Components Of IOT Devices Are:
- 1. Physical: object with embedded software into a hardware.
- 2. Hardware: consisting of a microcontroller, firmware, sensors, control unit, actuators and communication module.
- 3. Communication module: Software consisting of device APIs and device interface for communication over the network and communication circuit/port(s), and middleware for creating communication stacks using 6LowPAN, CoAP, LWM2M, IPv4, IPv6 and other protocols.
- 4. Software :for actions on messages, information and commands which the devices receive and then output to the actuators, which enable actions such as glowing LEDs, robotic hand movement etc.

Sensors: Sensors are electronic devices that sense the physical environments. An industrial automation system or robotic system has multiple smart sensors embedded in it. Sensor-actuator pairs are used in control systems. A smart sensor includes computing and communication circuits.
Control Units: Most commonly used control unit in IoT consists of a Microcontroller Unit (MCU) or a custom chip. A microcontroller is an integrated chip or core in a VLSI or SoC. Popular microcontrollers are ATmega 328, ATMega 32u4,Plc
An MCU comprises a processor, memory and several other hardware units which are interfaced together. It also has firmware, timers, interrupt controllers and functional IO units. Additionally.
Communication Module: communication enables to communicate other equipment todays plc and micro controller support many communication as like Ethernet,Modbus,Rs485,Opcua , Profinet, devicenet,Cc-link.
Software: IoT software consists of two components software at the IoT device and software at the IoT server.
What Is IT and OT:
Operation technology (OT) is the world of industrial plants and industrial control and automation equipment that include machines and systems to run the business, controllers, sensors, and actuators. Information technology (IT) is the world of end to-end information systems focusing on compute, data storage, and networking to support business operation in some context such as business process automation systems, customer relation management (CRM) systems, supply chain management systems, logistics systems, and human resources systems.
Often the final decision with the selection of communication systems, website hosting, and backup servers was the responsibility of the IT department.
OT relies on real-time data that drives safety, security, and control. It depends on very well-defined, tested, and trusted processes. Many plants need to run 24 × 7 with zero downtime (e.g., City Water Filtration System), and thus industrial processes cannot tolerate shutdown for software updates. IT is more lenient with software updates, introduction of new technologies, etc.
“When you take people with an IT background and bring them into an industrial control system environment, there’s a lack of understanding from operations
History of the Internet :
Before the advent of the Internet, the world’s main communication networks were based on circuit-switching technology: the traditional telephone circuit, wherein each telephone call is allocated a dedicated, end-to-end, electronic connection between the two communicating stations (stations might be telephones or computers). Circuit-switching technology was not suitable for computer networking. The history of the Internet begins with the development of electronic computers in the 1950s where the initial concepts of packet switching were introduced in several computer science laboratories. Various versions of packet switching were later announced in the 1960s. In the early 1980s, the TCP/IP (Transmission Control Protocol/Internet Protocol) stack was introduced. Then, the commercial use of the Internet started in the late 1980s. Later, the World Wide Web (WWW) became available in 1991, which made the Internet more popular and stimulated the rapid growth. The Web of Things (WoT), which based on WWW, is considered a part of IoT.

Security of IOT:
The security risks are also extremely serious when IoT devices are used in business enterprises. If an attacker hacks any of those smart objects that are used in a big enterprise, then the sensing capabilities that those smart objects have can be used by the attacker to spy on the enterprise. The Internet of Things (IoT) promises to make our lives more convenient by turning each physical object in our surrounding environment into a smart object that can sense the environment, communicate with the remaining smart objects, perform reasoning, and respond properly to changes in the surrounding environment. However, the conveniences that the IoT brings are also associated with new security risks and privacy issues that must be addressed properly. Ignoring these security and privacy issues will have serious effects on the different aspects of our lives including the homes we live in, the cars we ride to work, and even the effects that will reach our own bodies.
IOT Security Challenges:
- Multiple Technologies: IoT combines multiple technologies such as radiofrequency identification (RFID), wireless sensor networks, cloud computing, virtualization, etc. Each of these technologies has its own vulnerabilities.
- Multiple Verticals: The IoT paradigm will have numerous applications (also called verticals) that span eHealth, industrial, smart home gadgets, smart cities, etc. The security requirements of each vertical are quite different from the remaining verticals.
- Scalability: According to Cisco, 26.3 billion smart devices will be connected to the Internet by 2020. This huge number makes scalability an important issue.
- Big Data: Not only the number of smart objects will be huge, but also the data generated by each object will be enormous as each smart object is expected to be supplied by numerous sensors, where each sensor generates huge streams of data over time. This makes it essential to come up with efficient defensive mechanisms that can secure these large streams of data.
- Resource Limitations: The majority of IoT end devices have limited resource capabilities such as CPU, memory, storage, battery, and transmission range. This makes those devices a low-hanging-fruit for denial of service (DoS) attacks where the attacker can easily overwhelm the limited resource capabilities of those devices causing a service disruption. In addition to that, the resource limitations of those devices raise new challenges when it comes to developing secu8.2 IoT Security Challenges 214 rity protocols especially with the fact that the traditional and mature cryptography techniques are known to be computationally expensive
IOT Security Requirements:
- Confidentiality: ensures that the exchanged messages can be understood only by the intended entities.
- Integrity: ensures that the exchanged messages were not altered/tampered by a third party.
- Authentication: ensures that the entities involved in any operation are who they claim to be. A masquerade attack or an impersonation attack usually targets this requirement where an entity claims to be another identity.
- Availability: ensures that the service is not interrupted. Denial of service attacks target this requirement as they cause service disruption.
- Freshness: ensures that the data is fresh. Replay attacks target this requirement where an old message is replayed in order to return an entity into an old state.
- Authorization: ensures that entities have the required control permissions to perform the operation they request to perform.
- Non-repudiation: ensures that an entity can’t deny an action that it has performed.
- Forward Secrecy: ensures that when an object leaves the network, it will not understand the communications that are exchanged after its departure.
- Backward Secrecy: ensures that any new object that joins the network will not be able to understand the communications that were exchanged prior to joining the network.

Applications of IoT:
IoT Smart Building Solutions :As with smart homes (under smart energy), smart buildings utilize sensors and controllers to monitor and automatically trigger services to save valuable time in cases of emergency (e.g., fire, intrusion, or gas leak). With the smart building system, services like video monitoring, light control, air-condition control, and power supply control are often managed from the same control center. In this section, we will focus on smart buildings as an enterprise solution, as specified in the oneM2M standards.
IoT Finance: While IoT financial solutions are not as obvious as other IoT verticals, the financial industry has indeed benefited greatly from IoT. For many financial services businesses, the reality is that their business model is based on the flow of information, rather than on actual sensors and physical objects. As we mentioned in Chap. 1, some financial companies (e.g., Square, Intuit) have introduced IoT platform-based solutions connecting customers instantly with financial institutes and services. Such process used to be tedious and required time that often resulted in losing prospective deals to competitors. Banks are using IoT-based facial recognition solutions to identify important customers when they walk into the bank so they can be offered first-class treatment.
IoT Healthcare: Healthcare is considered as one of the most important verticals for IoT. Healthcare providers as well as patients are in great position to benefit from IoT. Intelligent IoT wearable devices in combination with mobile apps are allowing patients to capture their health data easily and send medical information for up to the minute analysis. Hospitals are using IoT for real-time tracking of important medical devices, personnel, and patients.
IoT Industrial : Industrial equipment and machines used in the overall manufacturing process, for instance, are becoming more digitized with capabilities to connect to the Internet. At the same time, manufacturers are looking at ways to advance operational efficiency such as supply chain and quality control, by utilizing such equipment to gather important data for their business to remain competitive and provide services at reasonable costs. IoT is used to establish networks between machines, humans, and the Internet, thereby creating new ecosystems.
IoT Retail: According to a survey by Infosys, more than 80% of consumers are willing to pay up to 25% more for a better experience. This translates to a huge opportunity to be gained with IoT by collecting and analyzing information about products and customer interests and then gaining actionable insights from this information. Input sources include point of sale (PoS), supply chain sensors, RFID, as well as video cameras in the store.
About TCP-IP:
Packet switching is a generic philosophy of network communication, not a specific protocol. The protocol used by the Internet is called TCP/IP. The TCP/IP protocol was invented by Robert Kahn and Vint Cerf. The IP in TCP/IP stands for Internet protocol: the protocol used by computers to communicate with each other on the Internet. TCP is responsible for the data delivery of a packet, and IP is responsible for the logical addressing. In other words, IP obtains the address, and TCP guarantees delivery of data to that address. Both technologies became the technical foundation of the Internet.
- The IP packets are independent of the underlying hardware structure. In order to travel across different types of networks, the packets are encapsulated into frames. The underlying hardware understands the particular frame format and can deliver the encapsulated packet.
- The TCP in TCP/IP stands for Transmission Control Protocol. This is a protocol that, as the name implies, is responsible for assembling the packets in the correct order and checking for missing packets. If packets are lost, the TCP endpoint requests new ones. It also checks for duplicate packets. The TCP endpoint is responsible for establishing the session between two computers on a network. The TCP and IP protocols work together.
- An important aspect of packet switching is that the packets have forwarding and return addresses. What should an address for a computer look like? Since it is a computer and computers only understand binary information, the most sensible addressing scheme is one based on binary numbers. Indeed, this is the case, and the addressing system used by IP version 4 software is based on a 32-bit IP address, and IP version 6 is based on 128-bit IP address .TCP/IP has four main layers: Application Layer, Transport Layer, Internet Layer, and Network Access Layer. Some researchers believe TCP/IP has five layers: Application Layer, Transport Layer, Network Layer, Data Link Layer, and Physical Layer. Conceptually both views are the same with Network Access being equivalent to Data Link Layer and Physical Layer combined
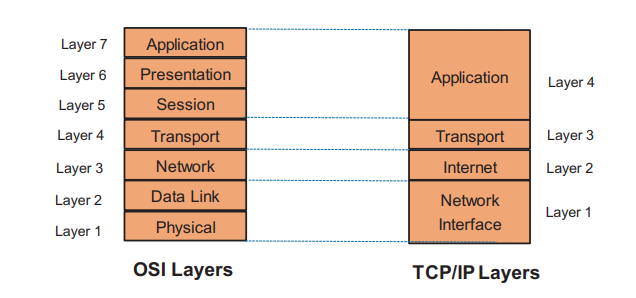
1) TCP/IP Layer 4: Application Layer As with the OSI model, the Application Layer is the topmost layer of TCP/IP model. It combines the Application, Presentation, and Session Layers of the OSI model. The Application Layer defines TCP/IP application protocols and how host programs interface with Transport Layer services to use the network.
2) TCP/IP Layer 3: Transport Layer The Transport Layer is the third layer of the four-layer TCP/IP model. Its main tenacity is to permit devices on the source and destination hosts to carry on a conversation. The Transport Layer defines the level of service and status of the connection used when transporting data. The main protocols included at the Transport Layer are TCP (Transmission Control Protocol) and UDP (User Datagram Protocol).
3) TCP/IP Layer 2: Internet Layer The Internet Layer of the TCP/IP stack packs data into data packets known as IP datagrams, which contain source and destination address information that is used to forward the datagrams between hosts and across networks. The Internet Layer is also responsible for routing of IP datagrams. The main protocols included at the Internet Layer are IP (Internet Protocol), ICMP (Internet Control Message Protocol), ARP (Address Resolution Protocol), RARP (Reverse Address Resolution Protocol), and IGMP (Internet Group Management Protocol).
4) TCP/IP Layer 1: Network Access Layer The Network Access Layer is the first layer of the four-layer TCP/IP model. It combines the Data Link and the Physical Layers of the OSI model. The Network Access Layer defines details of how data is physically sent through the network. This includes how bits are electrically or optically signaled by hardware devices that interface directly with a network medium, such as coaxial cable, optical fiber, radio links, or twisted pair copper wire. The most common protocol included in the Network Access Layer is Ethernet. Ethernet uses Carrier Sense Multiple Access/ Collision Detection (CSMA/CD) method to access the media, when Ethernet operates in a shared media. Such Access Method determines how a host will place data on the medium.
What Is OSI:
Reliable and efficient communication is considered one of the most complex tasks in large-scale networks. Nearly all data networks in use today are based on the Open Systems Interconnection (OSI) standard. The OSI model was introduced by the International Organization for Standardization (ISO), in 1984, to address this complex problem. ISO is a global federation of national standards organizations representing over 100 countries. The model is intended to describe and standardize the main communication functions of any telecommunication or computing system without regard to their underlying internal structure and technology. Its goal is the interoperability of diverse communication systems with standard protocols. The OSI is a conceptual model of how various components communicate in data-based networks. It uses “divide and conquer” concept to virtually break down network communication responsibilities into smaller functions, called layers, so they are easier to learn and develop. With well-defined standard interfaces between layers, OSI model supports modular engineering and multi-vendor interoperability.
The Open System Interconnection Model : The OSI model consists of seven layers as shown in Fig. : Physical (layer 1), Data Link (layer 2), Network (layer 3), Transport (layer 4), Session (layer 5), Presentation (layer 6), and Application (layer 7). Each layer provides some well defined services.
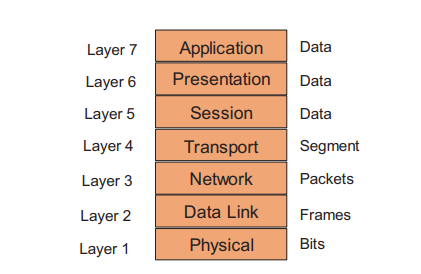
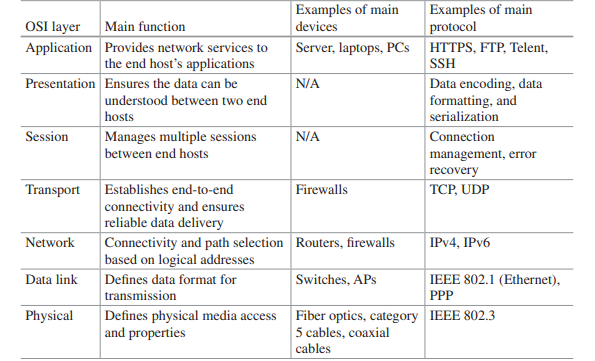
OSI Layer 7 – Application Layer: Starting from the top, the Application Layer is an abstraction layer that specifies the shared protocols and interface methods used by hosts in a communications network. It is where users interact with the network using higher-level protocols such as DNS (Domain Naming System), HTTP (Hypertext Transfer Protocol), Telnet, SSH, FTP (File Transfer Protocol), TFTP (Trivial File Transfer Protocol), SNMP (Simple Network Management Protocol), SMTP (Simple Mail Transfer Protocol), X Windows, RDP (Remote Desktop Protocol), etc.
OSI Layer 6 – Presentation Layer: Underneath the Application Layer is the Presentation Layer. This is where operating system services (e.g., Linux, Unix, Windows, MacOS) reside. The Presentation Layer is responsible for the delivery and formatting of information to the Application Layer for additional processing if required. It ensures that the data can be understood between the sender and receiver. Thus it is tasked with taking care of any issues that might arise where data sent from one system needs to be viewed in a different way by the other system. The Presentation Layer releases the Application Layer of concerns regarding syntactical differences in data representation within the end-user systems. Example of a presentation service would be the conversion of an EBCDICcoded text computer file to an ASCII-coded file and certain types of encryption such as Secure Sockets Layer (SSL) protocol.
OSI Layer 5 – Session Layer: Below the Presentation Layer is the Session Layer. The Session Layer deals with the communication to create and manage a session (or multiple sessions) between two network elements (e.g., a session between your computer and the server that your computer is getting information from).
OSI Layer 4 – Transport Layer: The Transport Layer establishes and manages the end-to-end communication between two end points. The Transport Layer breaks the data, it receives from the Session Layer, into smaller units called Segments. It also ensures reliable data delivery (e.g., error detection and retransmission where applicable). It uses the concept of windowing to decide how much information should be sent at a time between end points. Layer 4 main protocols include Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). TCP is used for guarantee delivery applications such as FTP and web browsing applications, whereas UDP is used for best effort applications such as IP telephony and video over IP.
OSI Layer 3 – Network Layer: The Network Layer provides connectivity and path selection (i.e., IP routing) based on logical addresses (i.e., IP addresses). Hence, routers operate at the Network Layer. The Network Layer breaks up the data it receives from the Transport Layer into packets, which are also known as IP datagrams, which contain source and destination IP address information that is used to forward the datagrams between hosts and across networks.1 The Network Layer is also responsible for routing of IP datagrams using IP addresses. A routing protocol specifies how routers communicate with each other, exchanging information that enables them to select routes between any two nodes on a computer network. Routing algorithms determine the specific choice of routes. Each router has a priori knowledge only of networks attached to it directly. A routing protocol shares this information first among immediate neighbors and then throughout the network. This way, routers gain knowledge of the topology of the network. The major routing protocol classes in IP networks will be covered in Sect.
OSI Layer 2 – Data Link Layer: The Data Link Layer defines data formats for final transmission. The Data Link Layer breaks up the data it receives into frames. It deals with delivery of frames between devices on the same LAN using Media Access Control (MAC) Addresses. Frames do not cross the boundaries of a local network. Internetwork routing is addressed by layer 3, allowing data link protocols to focus on local delivery, physical addressing, and media arbitration. In this way, the Data Link Layer is analogous to a neighborhood traffic cop; it endeavors to arbitrate between parties contending for access to a medium, without concern for their ultimate destination. The Data Link Layer typically has error detection (e.g., Cyclical Redundancy Check (CRC)). Typical Data Link Layer devices include switches, bridges, and wireless access points (APs). Examples of data link protocols are Ethernet for local area networks (multi-node) and the Point-to Point Protocol (PPP).
OSI Layer 1 – Physical Layer: The Physical Layer describes the physical media access and properties. It breaks up the data it receives from the Data Link Layer into bits of zeros and ones (or “off” and “on” signals). The Physical Layer basically defines the electrical or mechanical interface to the physical medium. It consists of the basic networking hardware transmission technologies. It principally deals with wiring and caballing. The Physical Layer defines the ways of transmitting raw bits over a physical link connecting network nodes including copper wires, fiber-optic cables, optical wavelength, and wireless frequencies. The Physical Layer determines how to put a stream of bits from the Data Link Layer on to the pins for a USB printer interface, an optical fiber transmitter, or a radio carrier.










